
Platform Single Sign-on for macOS
With Platform Single Sign-on (Platform SSO), you (or a developer that specializes in identity management) can build SSO extensions that allow users to use your organization’s account from an IdP on a Mac during the initial setup.
Features
Platform SSO supports the following features:
Activate and enforce Platform SSO during Automated Device Enrollment to authenticate the enrollment, sign in with a Managed Apple Account, and create a local user.
Provide a single sign-on experience for native and web apps.
Get information about Platform SSO in System Settings.
Synchronize passwords of local user accounts with the IdP, and define login policies.
Define group permissions of IdP accounts and allow people to use network-only IdP accounts at authorization prompts.
Create local user accounts on demand when logging in with credentials from an IdP account.
Support guest users who log in temporarily with their IdP credentials on shared Mac computers.
Note: Most features require support from the SSO extension. To learn more about implementing Platform SSO in your organization, consult your IdP’s documentation.
Requirements
A Mac with Apple silicon or an Intel-based Mac with Touch ID
A device management service that supports the Extensible Single Sign-on configuration, which includes settings for Platform SSO
An app containing a Platform SSO extension compatible with the IdP
macOS 13 or later
The following features have additional version requirements:
Feature | Minimum supported operating system version | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
Authenticated Guest Mode | macOS 26 | ||||||||||
Tap to Login | macOS 26 | ||||||||||
Platform SSO during Automated Device Enrollment | macOS 26 | ||||||||||
UPN prefix as local account name | macOS 15.4 | ||||||||||
Attestation for device identifiers | macOS 15.4 | ||||||||||
Login policies | macOS 15 | ||||||||||
On-demand account creation | macOS 14 | ||||||||||
Group management and network authorization | macOS 14 | ||||||||||
Platform SSO in System Settings | macOS 14 | ||||||||||
Platform SSO setup
To use Platform SSO, the Mac and each user needs to register with the IdP. Depending on IdP support and the applied configuration, the Mac can perform device registration silently in the background using:
A registration token provided in the device management configuration
An attestation, which provides a strong assurance about device identifiers (UDID and serial number)
To maintain a trusted connection with the IdP independent of the user, Platform SSO supports shared device keys. Use shared device keys whenever possible as they are required for features like Platform SSO during Automated Device Enrollment, on-demand creation of user accounts based on information from the IdP, network authorization, and Authenticated Guest Mode.
After a successful device registration, the user registers (unless the user account is using Authenticated Guest Mode). If the IdP requires it, user registration can involve prompting the user to confirm their registration. For local user accounts that Platform SSO creates on demand, user registration happens automatically in the background.
Note: If you unenroll a Mac from the device management service, it also unregisters from the IdP.
Authentication methods
Platform SSO supports different authentication methods with an IdP. Support for each depends on the IdP and the Platform SSO extension.
Password: With this method, a user authenticates with a local password or an IdP password. It also supports WS-Trust, which allows the user to authenticate even when the IdP managing their account is federated.
Secure Enclave–backed key: With this method, a user who logs in to their Mac can use a Secure Enclave–backed key to authenticate with the IdP without a password. The IdP sets up the Secure Enclave key during the user registration process.
Smart card: With this method, a user authenticates with the IdP using a smart card. To use this method, you need to:
Register the smart card with the IdP.
Configure smart card attribute mapping on the Mac.
For details and an example attribute mapping configuration, see the man page for Smart Card Services project.
Access key: With this method, users use a pass stored in Apple Wallet to authenticate with the IdP. Similar to a smart card, the access key needs to be registered with the IdP.
Certain functionalities, like creating user accounts on demand, require you to use a specific authentication method.
Feature | Password | Secure Enclave–backed key | Smart card | Access key | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
Group management | |||||||||||
Automated Device Enrollment | |||||||||||
Authenticated Guest Mode | |||||||||||
On-demand account creation | |||||||||||
Password synchronization | |||||||||||
Note: The SSO extension needs to support the requested method to perform the registration. Switching methods is also supported. For example, when a new user account is created during login with a user name and password, that account can then switch to use a Secure Enclave–backed key or smart card after the login is successful.
Platform SSO during Automated Device Enrollment
Organizations can activate and enforce Platform SSO during Setup Assistant with Automated Device Enrollment. This is an option for single-user devices because the user authenticating the enrollment automatically gets a local account created and can use SSO with supported native and web apps right away.
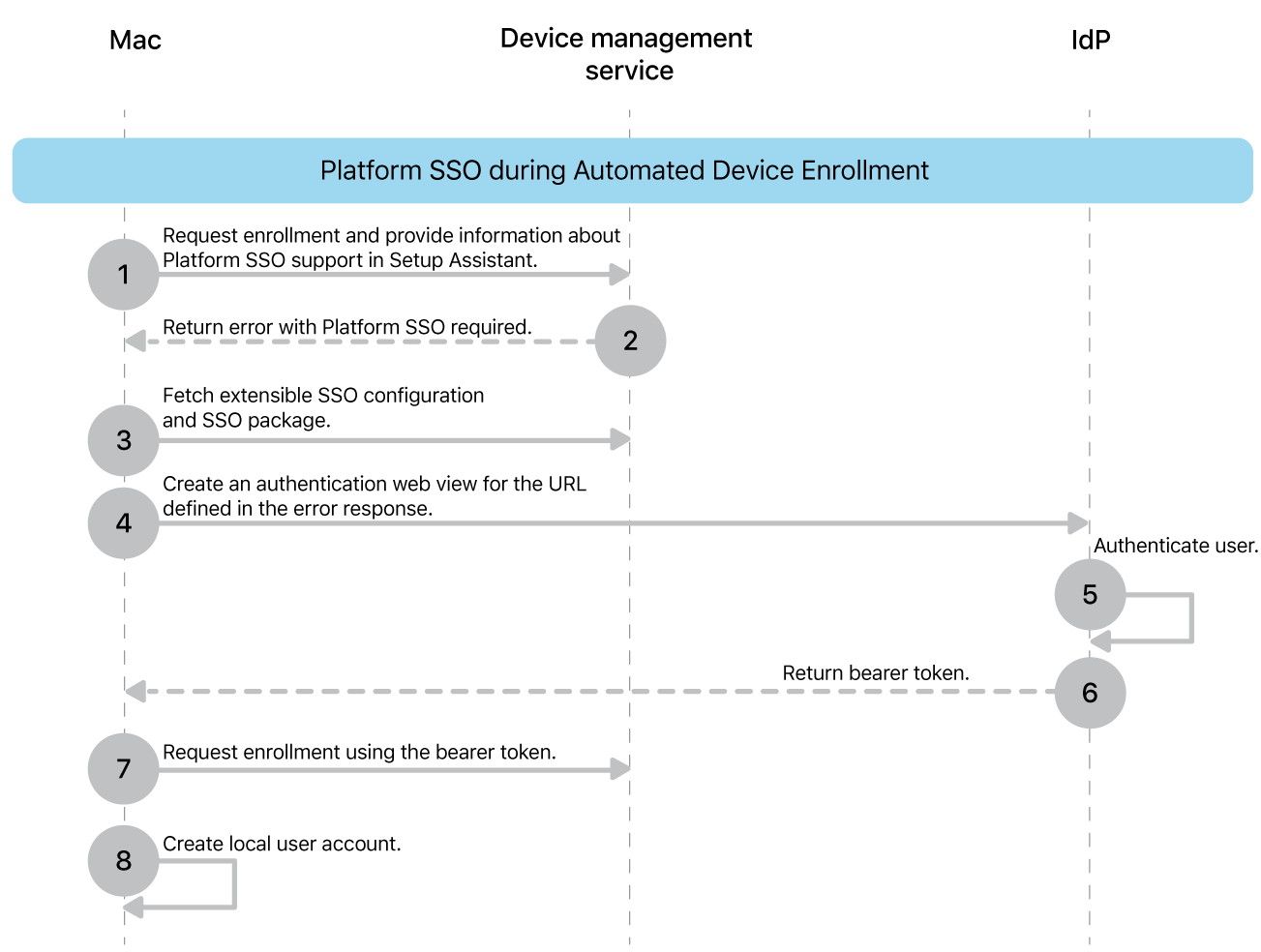
The process works like this:
macOS requests the enrollment and informs the device management service that it supports Platform SSO during enrollment.
The device management service returns a 403 error that includes information about where to find the SSO configuration and the package containing an app with the SSO extension.
macOS downloads and installs the Platform SSO extension and configuration.
macOS configures Platform SSO and performs a device registration. If attestation is configured, registration is done silently in the background. macOS then prompts the user to authenticate with their IdP using one of the methods listed earlier to do the user registration. Users can’t proceed without successful Platform SSO registration.
The IdP handles the authentication.
After a successful authentication, the IdP returns a bearer token to macOS.
macOS uses the bearer token to authenticate enrollment in the device management service, and—if federated to the same IdP—can sign the user in to their Managed Apple Account without having them enter their credentials again. For this to work, the iCloud Setup Assistant pane needs to be visible to the user.
macOS creates a local account, and the password either syncs with the IdP, or the user sets a local password (when Platform SSO uses a Secure Enclave–backed key). If necessary, you can enforce password complexity requirements for the local password using the Passcode configuration.
If configured, macOS can then sync the local account login profile picture from the IdP.
You can use Platform SSO during Automated Device Enrollment with an enforced software update. In this case, the device management service needs to enforce the update first.
If the user account that macOS creates is the only one on the Mac, it becomes an administrator account. If the device management service created an administrator account using the account configuration command, you can assign the user account different privileges using Platform SSO group management.
Single sign-on
Because Platform SSO is part of Extensible SSO, it provides the same single sign-on capabilities and allows users to log in once, then use the token provided by the initial authentication to authenticate with supported native and web apps.
If tokens are missing, expired, or more than four hours old, Platform SSO attempts to refresh or retrieve new ones from the IdP. Additionally, you can configure a duration in seconds (minimum 1 hour) until Platform SSO requires a full login instead of a token refresh. By default, a full login is required every 18 hours.
Platform SSO in System Settings
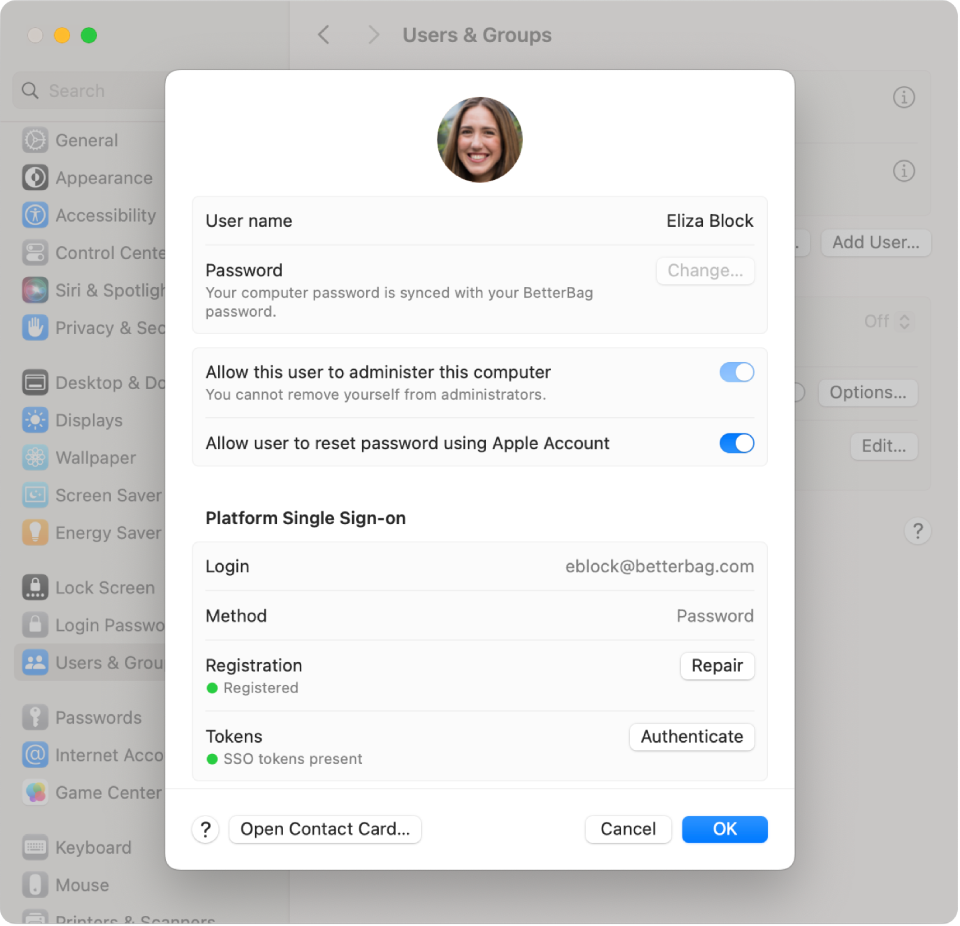
After Platform SSO is registered, a user can inspect the user registration status in System Settings > Users & Groups > [user name]. If necessary, they can initiate a repair of the registration and enforce a refresh of their authentication token.
The device registration status is visible in Users & Groups > Network account server and also offers an option to perform a repair.
Password synchronization and login policies
If you use the password authentication method, the local user password automatically syncs with the IdP whenever a user changes their password, either locally or remotely. If necessary, macOS prompts the user for their previous password.
By default, the local account password is required to unlock FileVault, the Lock Screen, and at the login window. If the entered password doesn’t match the password of the local user account, macOS attempts to reach the IdP to perform a live authentication. If macOS is unable to reach the IdP or the entered password doesn’t match the password stored by the IdP, authentication fails.
With login policies, you can allow the use of the current account password from the IdP at these three prompts immediately. You can also set the following policies individually for FileVault, Lock Screen, and the login window:
Attempt authentication.
If configured, there’s an attempt at live authentication with the IdP.
If the Mac is online, a successful authentication with the IdP is required to proceed, even when the Mac is offline after the first attempt.
If authentication is successful, Platform SSO updates the local password.
If the Mac is offline, the user can use their local account password.
Require authentication.
If configured, live authentication with the IdP is required to proceed.
If the Mac is online, a successful authentication with the IdP is required to proceed, regardless of a configured offline grace period.
If authentication is successful, Platform SSO updates the local password.
If the Mac is offline, users can’t log in. In those situations, you can enable an offline grace period and set it to the amount of days after a previous successful login, during which time the user can continue to use the local account password.
You can define if any account logging in to the Mac needs to be managed by Platform SSO or if login with local-only accounts is still allowed. It’s also possible to define the amount of days after the policy is applied or updated until when this setting is enforced. This allows the temporary use of local accounts. For example, you can temporarily use an administrator account created by the device management service to perform or repair the Platform SSO device registration.
Instead of live authentication, you can also allow users to use Touch ID or Apple Watch on the Lock Screen.
If necessary, local accounts (as defined by you) can be exempt from login policies and not prompted to register for Platform SSO.
Group management and network authorization
Platform SSO offers granular rights management to provide users with the right level of privileges they need on their Mac. To do so, Platform SSO can apply the following privileges to an account each time the user authenticates:
Standard: The account gets standard user privileges.
Administrator: Adds the account to the local administrator group.
Groups: Define privileges by group membership, which update every time the user authenticates with the IdP.
When you use groups, an account gets privileges based on membership of the following:
Administrator groups: If the account is part of a listed group, they have local administrator access.
Authorization groups: If the account is part of a group assigned to a built-in or custom-defined authorization right, then the account has privileges associated with that group. For example, macOS uses the following authorization rights:
system.preferences.datetime, which allows the account to modify time settings.system.preferences.energysaver, which allows the account to modify energy saver settings.system.preferences.network, which allows the account to modify network settings.system.preferences.printing, which allows the account to add or remove printers.
Additional groups: Custom-defined groups for macOS or specific apps, which macOS creates automatically inside the local directory (if they don’t already exist). For example, you can use an additional group in the
sudoconfiguration to definesudoaccess.
Network authorization
Platform SSO expands the use of IdP credentials to users who don’t have a local account on the Mac for authorization purposes. These accounts use the same groups as group management. For example, if the account is a member of one of the administrator groups, it can perform administrator authorization prompts. To use this functionality, configure Platform SSO with shared device keys.
Network authorization isn’t possible with authorization prompts that require a secure token, ownership permissions, or authentication by the current logged-in user.
On-demand account creation
To facilitate account management in shared deployments, users can use their IdP user name and password or a smart card to log in to a Mac to create a local account.
You can achieve a fully automated provisioning process using Automated Device Enrollment with Auto Advance. You need to create the first local administrator account using a device management service, and perform silent Platform SSO registration.
The following are required to use on-demand account creation:
Enroll the Mac in a device management service that supports bootstrap tokens.
Add the following: an SSO extension configuration with Platform SSO, shared device keys, and the option to create a user at login.
Complete Setup Assistant and create a local administrator account.
Have the Mac at the login window with FileVault unlocked and a network connection.
Using an optional configuration option, you can define which attribute from the IdP to use for the local account name (often called the user’s short name) and full name. Administrators can also set the key for the account name to com.apple.PlatformSSO.AccountShortName to use the UPN prefix.
Additionally, you can define what privileges to apply to newly created accounts at login. The same options for group management are available:
Standard: The account gets standard user privileges.
Administrator: Adds the account to the local administrator group.
Groups: Define privileges by group membership, which update every time the user authenticates with the IdP.
Authenticated Guest Mode
Authenticated Guest Mode provides an expedited login experience for shared deployments, such as medical offices or schools, where different users donʼt need a local account created, because they just need to sign in with their IdP credentials for a short period of time. The user gets standard user privileges by default, but you can change those privileges using Platform SSO group management.
To use this feature, you need the same requirements as on-demand account creation but instead of the option to create a user at login, you configure Authenticated Guest Mode.
When a user logs out, macOS erases all local data for that account, and the shared Mac is ready for the next user to log in.
Tap to Login
Tap to Login extends the digital credential functionality from Apple Wallet to macOS. Over the past few years, organizations have adopted digital badges in Apple Wallet, allowing users to unlock doors with just the tap of an iPhone or Apple Watch without needing the physical badge. This same experience is available on a Mac.
This authentication method is particularly valuable for organizations that share a Mac across multiple users, including educational institutions, retail environments, and healthcare facilities.
With Tap to Login, users can authenticate on a Mac configured for Authenticated Guest Mode when they tap their iPhone or Apple Watch on an attached NFC reader. This initiates a secure single sign-on process that automatically authenticates users to their apps and websites, allowing them to quickly log in and get to work.
User credentials are provisioned as access keys in an Apple Wallet pass through an iPhone app or browser. These access keys are stored in the device’s Secure Enclave, making them hardware-backed, and encrypted, and helping to protect from tampering or extraction attempts. Express Mode functionality enhances convenience by allowing for immediate authentication without requiring users to wake or unlock their device, similar to how transit cards work in Apple Wallet.
To implement Tap to Login functionality, a Mac needs to be:
Configured for Authenticated Guest Mode
Equipped with a supported external NFC reader
Access key creation and management requires participation in the Apple Wallet Access Program. For more information on how to create an access key, see Provisioning in the Apple Wallet Access Program Guide.

